Navigating the nexus of Policy, Digital Technologies, and Futures (S1/E14)
S1/E14: Bonus Episode – The EU Cybersecurity Resilience Act
Hello dear readers! I’ve decided to follow a suggestion by our colleague John Favaro and bring you two bonus tracks – same player shoots again! (for those of my age…). So, welcome to this first postface to our blog series, where I’ll fill the gap left open by the Cyber Resilience Act, which is officially known as Horizontal cybersecurity requirements for products with digital elements.
We can all agree that in an ever-evolving digital world, cybersecurity has become a paramount concern for governments, businesses, and individuals alike. The European Commission (EC) has taken a proactive approach to address the growing cyber threats with the introduction of several legislation proposals, including this one, namely the EU Cybersecurity Resilience Act (CRA). In this blog post, I will explore its key provisions and implications for the software industry. Since the Act hasn’t been approved yet, I will address both the EC proposal and the current reactions by the EU Council and the European Parliament (EP).
Main provisions
The proposed CRA text establishes stricter obligations for software providers to ensure the security of their products and services. Under this Act, software companies are to be required to adopt a risk-based approach to cybersecurity, identifying potential threats and vulnerabilities and implementing appropriate security measures to mitigate them. This proactive approach should promote a culture of security-first software development, safeguarding users from potential cyber-attacks. The CRA aims to safeguard consumers and businesses buying or using products or software with a digital component, in particular those described as being part of the Internet of Things (IoT).
The problem addressed by the proposed regulation is two-fold. Firstly, there is the insufficient level of cybersecurity that is inherent in many products, which inadequate security updates to such products and software don’t help. Secondly, there is our collective inability, as consumers or businesses, to currently determine which products are cybersecure, or to set them up in a way that ensures their cybersecurity is protected. These are very important, as shown by, lest we forget, the Mirai botnet attack in 2016, which mainly targeted consumer devices such as CCTV cameras and home routers that were connected the Internet.
The proposed Cyber Resilience Act would hence guarantee:
- harmonised rules when bringing to market products or software with a digital component;
- a framework of cybersecurity requirements governing the planning, design, development and maintenance of such products, with obligations to be met at every stage of the value chain (yes, even if your suppliers are based outside the Union);
- an obligation to provide duty of care for the entire lifecycle of such products.
It was proposed that, when the regulation enters into force, CRA-compliant software and products connected to the internet would bear the CE marking to indicate that they are secure by explicit cybersecurity standards.
The proposed regulation would apply to all products connected directly or indirectly to another device or to a digital network, except for specified exclusions such as open-source software or yet services that are already covered by existing rules, which is the case for, e.g., medical devices, aviation, and cars.
Some detail
If you happen to be in the IoT business, which can be a very large sector, depending on its definition, you’d wish to have a close look at the CRA proposal and its current discussions at the EU Council and the EP. This is because such an area will be heavily regulated as a result of this law.
Here are a few important new features regulating the IoT domain.
- Cybersecurity must be taken into account in all phases of the product: planning, design, development, production, delivery, and maintenance.
- All cybersecurity risks are documented.
- Manufacturers will have to report actively exploited vulnerabilities and incidents.
- Once a product is sold, manufacturers must ensure that for the expected product lifetime, or for a period of five years (whichever is the shorter), vulnerabilities are handled effectively.
- Products must carry clear and understandable instructions for their use.
- Security updates must be made available for at least five years.
It’s said that a picture is worth a thousand words. (In terms of bytes, it’s actually much more than that.) In any case, here is how the EC presented the CRA’s enforcement in practice, in its accompanying Factsheet. It gives an idea of who’s expected to be caught in the regulation net.
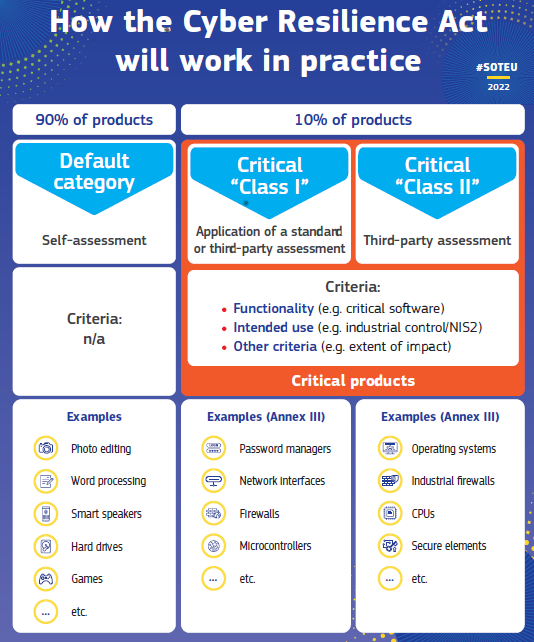
The noble intention of the EC proposal is that the Act would see inadequate security features become a thing of the past, with the introduction of mandatory cybersecurity requirements for manufacturers and retailers of such products, with this protection extending throughout the product’s lifecycle and its supply chain. But, as we all know, the devil’s in the details, here meaning enforcement, compliance, and unintended consequences. While the intention behind this legislation is commendable, it is essential to analyse its actual impact on the software industry ecosystem and the potential challenges it poses.
For a starter, as you may imagine, this legislation will heavily interweave with the Data and AI Acts. As I heard from an EC official during a meeting in Brussels: On Artificial Intelligence, one could say that the CRA is about the content, while the AI Act is about the procedures. It’s also intertwined with NIS2, the Cybersecurity Act, and other legislations mentioned and not mentioned before in this blog series. Lawyers of the world: Rejoice!
The proposal by the European Commission – The bright side of things
There are many positive points in the CRA. One of the significant impacts of the proposal on the digital industry is the introduction of mandatory certification and compliance requirements. Providers of digital products would have to undergo rigorous assessments to obtain a cybersecurity certification that attests to the safety and reliability of their products. This certification is meant to enhance the industry's overall credibility, fostering trust among customers and businesses, while boosting competitiveness within the EU market.
In addition, the Act mandates that software companies promptly report any cybersecurity incidents to relevant authorities and affected customers. This provision aims at increasing transparency and accountability, enabling authorities to respond swiftly to cyber threats and offering users crucial information about potential risks they may face. While incident reporting can pose challenges for businesses, it ultimately contributes to a collective effort in fortifying the EU's cybersecurity infrastructure.
The proposal also emphasizes collaboration among digital products providers, cybersecurity experts, and governmental bodies. Such open exchanges of information enable faster threat detection, sharing of best practices, and a coordinated response to emerging cyber threats. To facilitate such information exchanges, the proposal tries to establish clear guidelines to protect proprietary information.
Finally, by setting clear standards and guidelines, the proposal wanted to provide a strong foundation for innovative cybersecurity solutions, encouraging companies to invest in cutting-edge technologies that can withstand emerging threats, ensuring that the EU remains at the forefront of global cybersecurity advancements.
The proposal by the European Commission – The world isn’t that rosy
On the other hand, several pitfalls exist in the proposal. As we discussed before in past episodes, while larger corporations have the resources and expertise to comply with stringent cybersecurity obligations, smaller software companies, particularly SMEs, are likely to face considerable challenges. The proposal's complex certification and compliance requirements might prove overwhelming for smaller players, hindering their ability to compete within the EU market. Consequently, this legislation risks stifling innovation and market diversity, favouring again big tech companies and further consolidating their market dominance.
As it happens, the proposed EU Cybersecurity Resilience Act imposes significant costs on software companies, particularly when it comes to obtaining and maintaining the mandatory cybersecurity certifications. These compliance costs can be prohibitive for businesses operating on tight budgets, diverting resources away from research, development, and improvement of their products. In some cases, these financial burdens might force companies to cut corners on different aspects of security.
While the Act sets out cybersecurity obligations, it lacks clarity in terms of implementation and enforcement. This ambiguity can lead to inconsistent interpretations of the requirements, creating confusion among digital products providers and regulatory authorities alike. For instance, what happens to a product that has already been certified, and carries a CE label to attest this, when it receives a software update? Does it have to be certified again? The CE label magically disappears if so? As a result, some companies may accidentally fall short of compliance, exposing themselves to penalties and legal consequences. The lack of clear guidelines could also lead to potential loopholes, undermining the Act's very purpose.
In addition, companies may feel constrained by the rigid requirements, concerning specific security standards and measures, making it challenging to develop cutting-edge technologies in cybersecurity or IoT, for lack of room for experimentation and adaptation to rapidly changing technologies. Consequently, such a piece of legislation, along with its siblings, might inadvertently hamper the EU digital industry's ability to innovate.
Finally, the Act's stringent cybersecurity requirements might even lead to trade barriers and strained international relations. This is because companies operating outside the EU may find it challenging to align their products with the EU standards, potentially limiting market access and world-wide collaborations, jeopardising global supply chains. Moreover, this legislation could lead to disputes over data protection and security standards in international trade agreements, potentially triggering retaliatory measures from other countries.
Reactions from the EU Council and the European Parliament
Remember that the EU co-legislators have yet to start negotiating the CRA. The following analysis of their current positions is adapted from the text in the EP’s very own website.
In the Council, a progress report was presented in December 2022 by the Czech Presidency. The Council welcomed the CRA proposal, but expressed a need to clarify its scope to make it explicit whether software as a service is part of it. They proposed the exclusion of products exclusively intended for military purposes from the scope of the proposal, and expressed a need to clarify interactions with other legislative acts, namely with the Directive on the Security of Network and Information Systems (NIS2) and the Cybersecurity Act (CSA). They also expressed a need to evaluate the burden of the proposal for the industry, in particular for SMEs, and to elaborate on the role of the European Union Agency for Cybersecurity (ENISA). In June 2023 the Swedish Presidency progress report on the proposal was presented. It identified several points to be further discussed, namely the classification of products with digital elements with regards to their sensitivity and the related list, the conformity assessment provisions, and the reporting obligations. Status of open-source components and Software-as-a-Service, impact on the SMEs, and lack of available harmonised standards, were also of concern.
At the other side of Brussels, the EP draft report was published in March 2023. The Rapporteur proposed, among other things, to clarify the scope of the regulation (e.g. by excluding products with digital elements intended to process classified information and open-source software supplied outside the framework of a commercial activity); to review the product lifetime concerning the vulnerability handling (remove a fixed date for expected product lifetime); to align reporting obligations with the NIS2 directive and to centralise reporting of significant security incidents within ENISA; to include home automation systems and security devices into the list of critical products under Class I; to extend the transition period for the application of the regulation, so that in particular micro-small-medium-enterprises will have sufficient time to adapt; and to allocate the penalties issued under the CRA to the Digital Europe Programme, with the aim to raise the overall cybersecurity level across the EU.
What to say?
The proposed EU Cybersecurity Resilience Act certainly marks a significant step forward in securing the digital landscape for individuals, businesses, and governments across the European Union. Its impact on the digital industry will again be transformative, forcing a culture of security, accountability, and collaboration. As the digital sector adapts to these new requirements, the result will likely be a safer and more resilient ecosystem, where innovation may thrive without compromising cybersecurity. By prioritising the protection of data and digital infrastructure, the EU sets a strong example for the rest of the world, highlighting the importance of proactive cybersecurity measures in the digital age.
However, the Act does come with both positive and negative consequences. While users and larger corporations might benefit from increased security measures and improved market credibility, SMEs and innovative start-ups may face significant challenges in complying with its costly and complex requirements. Ambiguity in implementation and enforcement, potential impacts on innovation, and possible but little understood global impact raise concerns about the Act's overall effectiveness.
I hope that this (long) bonus episode helps the readers to get an idea about what is coming next from the EU in the form of the Cybersecurity Resilience Act, once it’s approved by the co-legislators. It’s very ambitious and encompassing. You can’t hide and you can’t run.
The second bonus episode will bring a brief explanation of Horizon Europe, the current EU Framework Programme for Research and Innovation, which is, after all, another regulation of the European Union. If you're interested in a Horizon beginners tour, stay tuned!
Keep well!
[This blog series is inspired by research work that is or was partially supported by the European research projects CyberSec4Europe (H2020 GA 830929), LeADS (H2020 GA 956562), and DUCA (Horizon Europe GA 101086308), and the CNRS International Research Network EU-CHECK.]
CNRS - France
Digital Skippers Europe (DS-Europe)




2fdck for sale | 2-fdck for sale | order 2fdck online UK US AUS
2-fdck for sale 2fdck for sale where to buy 2fdck ? legit 2fdck sellers , 2fdck suppliers in canada USA UK Buy 2fdck online | Order 2fdck online AUS canada UK | 2fdck price per gram 2fdck for sale https://buy2cbonline.com/product/2-fdck-for-sale/
2-FDCK, or 2-Fluorodeschloroketamine, is a dissociative anesthetic that's chemically related to ketamine.